Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF)
CrossSite Scripting XSS and CrossSite Request Forgery CSRF are common web security vulnerabilities but they exploit...
%20and%20Cross-Site%20Request%20Forgery%20(CSRF).jpg)
Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF):🔗
Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) are both common web security vulnerabilities, but they exploit different weaknesses and require different protections. Let's explore each with examples.
Cross-Site Scripting (XSS) Attack🔗
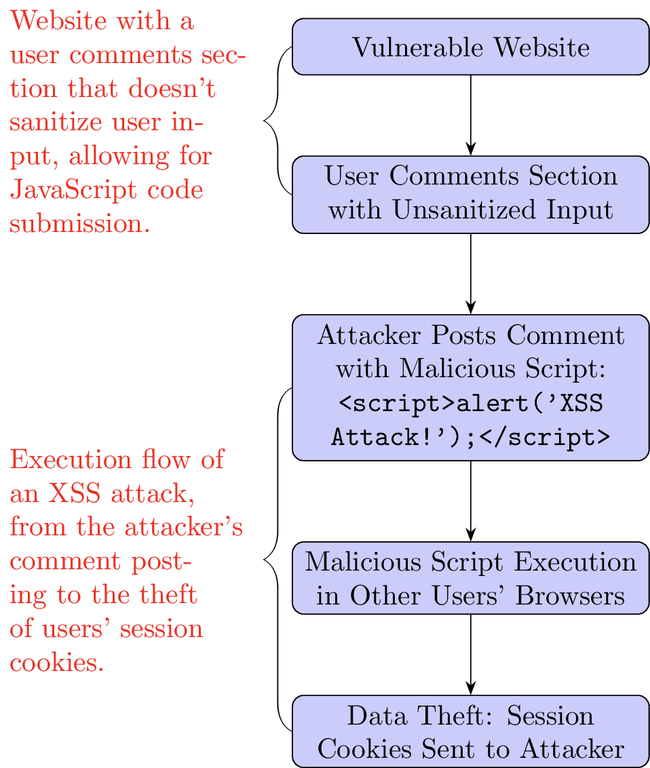
What is XSS?
XSS attacks involve injecting malicious scripts into content that gets served to other users. These scripts run in the context of the user's browser and can steal cookies, session tokens, or other sensitive information exposed through client-side scripts.
Example Scenario:
-
Vulnerable Website: Imagine a website with a user comments section that doesn't properly sanitize user input. This means users can submit comments with JavaScript code.
-
Attack Execution: An attacker posts a comment containing a malicious script:
<script>alert('XSS Attack!');</script>. -
Script Execution: When other users view the comment, the malicious script executes in their browsers. If the script were designed to steal cookies, it could send the user's session cookie to the attacker.
-
Data Theft: The attacker uses the stolen session cookie to impersonate the victim, gaining unauthorized access to their account.
Prevention:
- Sanitize user input by escaping special characters.
- Use Content Security Policy (CSP) headers to restrict sources of executable scripts.
- Employ anti-XSS libraries and tools.
Cross-Site Request Forgery (CSRF) Attack🔗
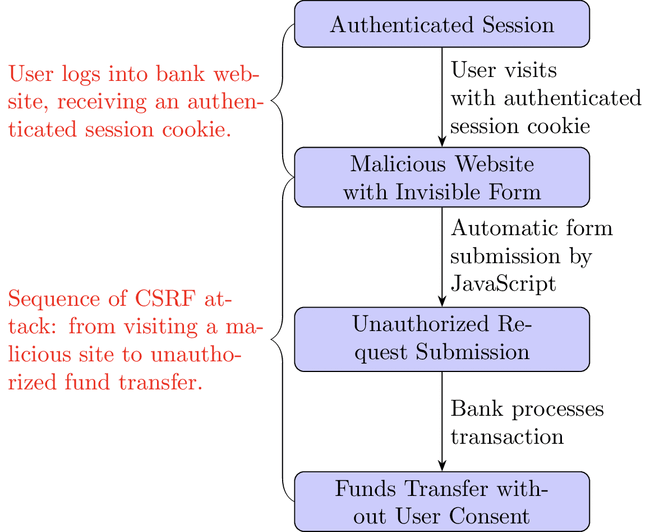
What is CSRF?
CSRF attacks trick a user into submitting a request to a different website where they are authenticated, without their knowledge or intention. This exploits the trust a site has in the user's browser.
Example Scenario:
-
Authenticated Session: A user logs into their bank website, which uses cookies for session management. The user's browser now has an authenticated session cookie.
-
Malicious Website: The user then visits a malicious site, which contains an invisible form that's automatically submitted by JavaScript:
<form action="https://bank.com/transfer" method="POST"><input type="hidden" name="amount" value="1000"/><input type="hidden" name="account" value="attacker"/></form><script>document.forms[0].submit();</script>. -
Unauthorized Request: The form submission is made to the bank's website from the user's browser, with the user's authenticated session cookie automatically included. If the bank's website doesn't properly verify the origin of the request, it will process the transaction as if the user intended it.
-
Funds Transfer: The attacker successfully transfers funds from the user's account to their own without the user's consent.
Prevention:
- Use anti-CSRF tokens in forms that change server state. These tokens should be unique per session and validated on the server side.
- Check the
RefererandOriginheaders to ensure requests are coming from trusted sources. - Implement SameSite cookie attributes to control when cookies should be sent with cross-site requests.
Key Differences:🔗
- XSS exploits the trust a user has in a particular site, executing malicious scripts in the user's browser.
- CSRF exploits the trust a site has in the user's browser, making unauthorized requests on behalf of the user.
COMING SOON ! ! !
Till Then, you can Subscribe to Us.
Get the latest updates, exclusive content and special offers delivered directly to your mailbox. Subscribe now!